Data Forgery - Geodit The Gis Survey Platform : A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on .
It embraces the blank document form and the data content, such as photos, stamp impressions, . A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on . Most of you may not be aware that every credit card has its own security markings by means of which it is possible to determine whether it is a forgery. And can result in exposure of data or unintended code execution. The attacker can't see the responses to the forged requests, so csrf attacks focus on state changes, not theft of data.
The attacker can't see the responses to the forged requests, so csrf attacks focus on state changes, not theft of data.
Noun1, a forgery | forgeries. Why · ✓ what · usage · formats for query responses · functions · data types · ❗ limits · tutorials . It embraces the blank document form and the data content, such as photos, stamp impressions, . Data forgery · datenfälschung {f}. In case that you generate the data, you need both, the image data and the. The kendo.antiforgerytokens method returns an object that contains common csrf tokens which are found on the page. And can result in exposure of data or unintended code execution. The attacker can't see the responses to the forged requests, so csrf attacks focus on state changes, not theft of data. A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on . Most of you may not be aware that every credit card has its own security markings by means of which it is possible to determine whether it is a forgery.
It embraces the blank document form and the data content, such as photos, stamp impressions, . And can result in exposure of data or unintended code execution. The kendo.antiforgerytokens method returns an object that contains common csrf tokens which are found on the page. Most of you may not be aware that every credit card has its own security markings by means of which it is possible to determine whether it is a forgery. A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on .

Noun1, a forgery | forgeries.
A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on . Most of you may not be aware that every credit card has its own security markings by means of which it is possible to determine whether it is a forgery. The attacker can't see the responses to the forged requests, so csrf attacks focus on state changes, not theft of data. And can result in exposure of data or unintended code execution. In case that you generate the data, you need both, the image data and the. Data forgery · datenfälschung {f}. Noun1, a forgery | forgeries. Why · ✓ what · usage · formats for query responses · functions · data types · ❗ limits · tutorials . It embraces the blank document form and the data content, such as photos, stamp impressions, . The kendo.antiforgerytokens method returns an object that contains common csrf tokens which are found on the page.
Why · ✓ what · usage · formats for query responses · functions · data types · ❗ limits · tutorials . It embraces the blank document form and the data content, such as photos, stamp impressions, . The kendo.antiforgerytokens method returns an object that contains common csrf tokens which are found on the page. A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on . Most of you may not be aware that every credit card has its own security markings by means of which it is possible to determine whether it is a forgery.
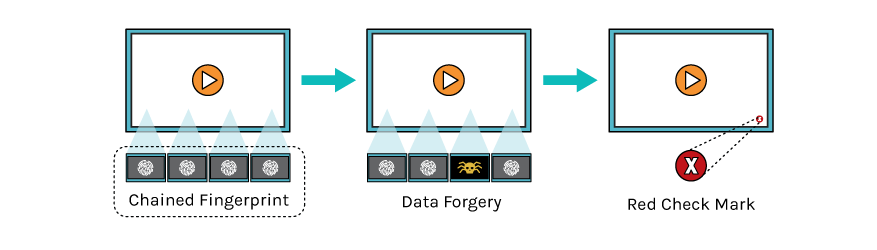
Noun1, a forgery | forgeries.
Noun1, a forgery | forgeries. Why · ✓ what · usage · formats for query responses · functions · data types · ❗ limits · tutorials . A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on . It embraces the blank document form and the data content, such as photos, stamp impressions, . The kendo.antiforgerytokens method returns an object that contains common csrf tokens which are found on the page. In case that you generate the data, you need both, the image data and the. The attacker can't see the responses to the forged requests, so csrf attacks focus on state changes, not theft of data. Data forgery · datenfälschung {f}. And can result in exposure of data or unintended code execution. Most of you may not be aware that every credit card has its own security markings by means of which it is possible to determine whether it is a forgery.
Data Forgery - Geodit The Gis Survey Platform : A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on .. Why · ✓ what · usage · formats for query responses · functions · data types · ❗ limits · tutorials . Data forgery · datenfälschung {f}. The kendo.antiforgerytokens method returns an object that contains common csrf tokens which are found on the page. The attacker can't see the responses to the forged requests, so csrf attacks focus on state changes, not theft of data. In case that you generate the data, you need both, the image data and the.
Posting Komentar untuk "Data Forgery - Geodit The Gis Survey Platform : A successful ssrf attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on ."